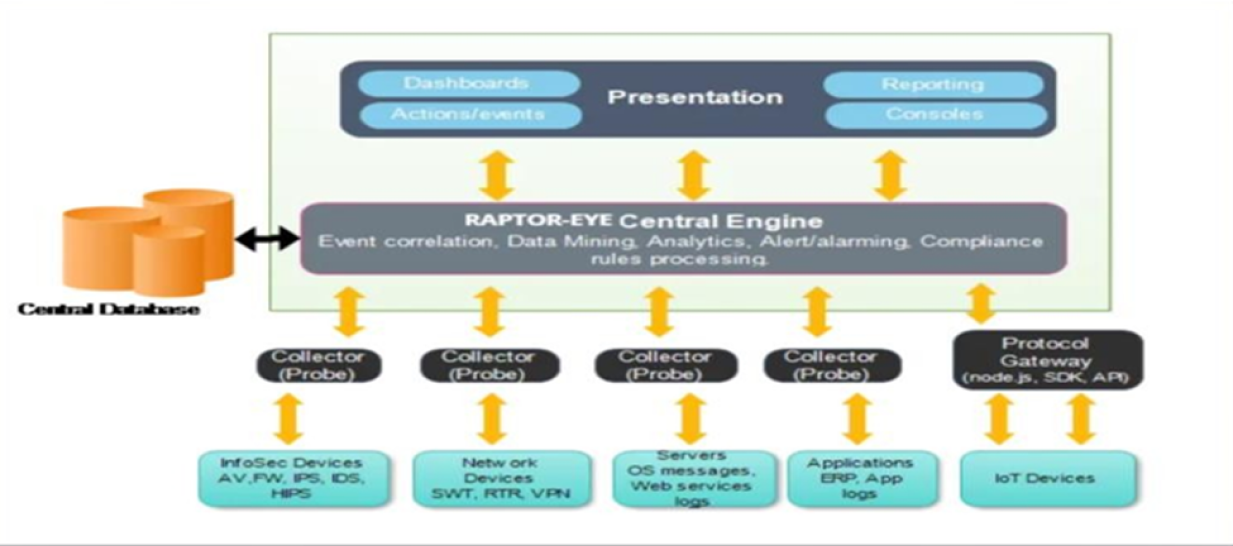
How To Integrate IOT & OT With Raptor Eye
Integrating IoT (Internet of Things) with RAPTOR-EYE (Security Information and Event Management) systems can enhance security monitoring and threat detection capabilities, especially in environments where IoT devices are prevalent. Here's how you can integrate them:
- Collecting IoT Data: IoT devices generate vast amounts of data related to their operations and interactions. This data can include device status, sensor readings, network traffic, and more. Integrate your RAPTOR-EYE system with IoT data sources to collect this information in real-time or at regular intervals.
- Normalization and Parsing: IoT data may come in various formats and protocols depending on the devices and their manufacturers. Normalize and parse this data within the RAPTOR-EYE platform to ensure consistency and compatibility for analysis and correlation with other security events.
- Correlation and Analysis: Leverage the correlation capabilities of the RAPTOR-EYE to analyze IoT data alongside other security events and logs from IT infrastructure, applications, and networks. Look for patterns, anomalies, and indicators of compromise (IoCs) that could indicate potential security threats or incidents involving IoT devices.
- Behavioral Analytics: Use behavioral analytics to establish baselines of normal behavior for IoT devices and detect deviations from these baselines that may indicate security incidents such as unauthorized access, data exfiltration, or malware infections.
- Threat Intelligence Integration: Integrate threat intelligence feeds with your RAPTOR-EYE to enrich IoT data analysis. This can help identify known malicious IPs, domains, or signatures associated with IoT-related threats and attacks.
- Incident Response and Automation: Develop incident response procedures and automated workflows tailored to IoT security incidents. This may include actions such as isolating compromised devices, blocking malicious traffic, or triggering alerts for further investigation.
- Compliance and Reporting: Use RAPTOR-EYE capabilities to generate compliance reports related to IoT security standards and regulations. This ensures that your organization meets regulatory requirements and can demonstrate the security posture of its IoT infrastructure.
- Continuous Monitoring and Adaptation: Implement continuous monitoring of IoT devices and adjust your RAPTOR-EYE configurations and detection rules as the IoT landscape evolves and new threats emerge. Regularly review and update your integration to stay ahead of potential security risks.