Raptor Eye's cybersecurity solution in Saudi Arabia significantly reduces the risk of cybercrime and security issues. It safeguards an organization's network status and facilitates the creation of new network nodes while enhancing its existing system. The features include
Raptor Eye Agent, a lightweight agent, collects data from endpoints and sends it to the Raptor Eye Manager for correlation.
Raptor Eye Manager receives data from Raptor Eye Agents and end devices, performing correlation to identify potential threats.
Raptor Eye, a leading cybersecurity solution provider Saudi Arabia, excels in the meticulous collection, classification, and indexing of file properties and content. It skillfully manages permissions
and hierarchies within file and folder structures across various data repositories. Through real-time aggregation, normalization, and enrichment of access events, Raptor Eye captures comprehensive insights about user activities and
directory services, providing a solid foundation for in-depth security analysis.
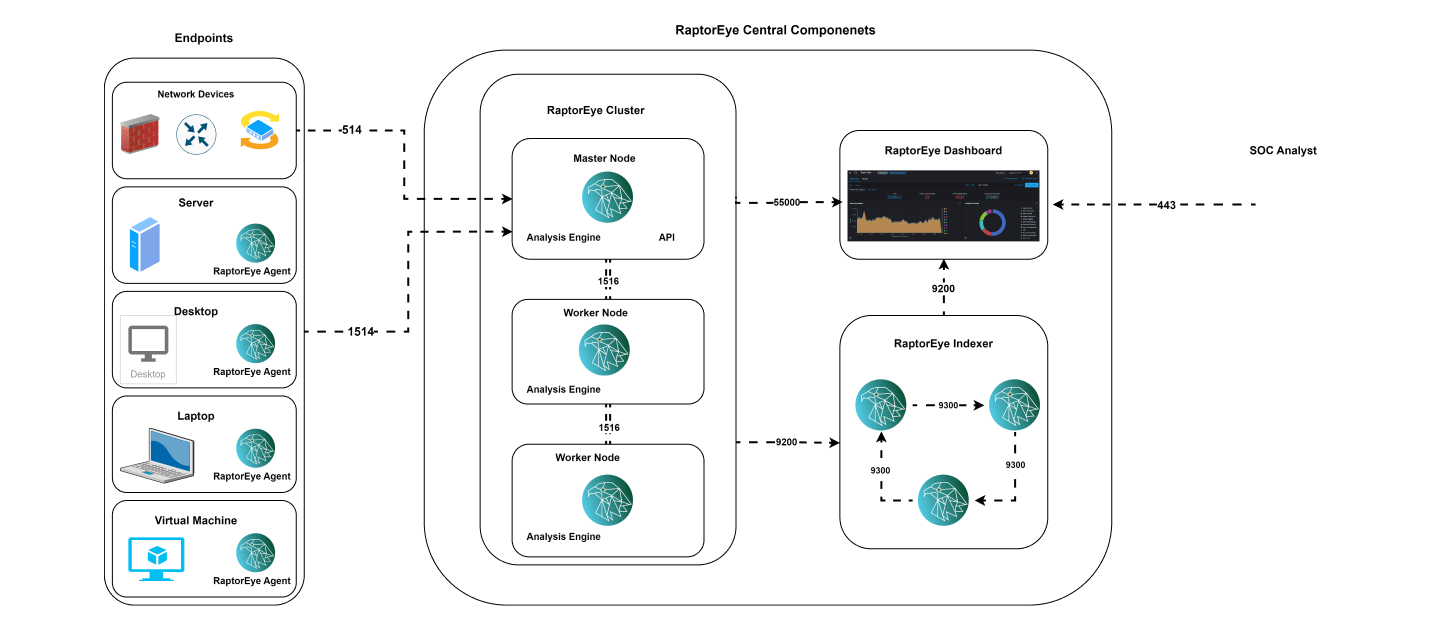
Raptor Eye, a leading cybersecurity solution provider Saudi Arabia, excels in the meticulous collection, classification, and indexing of file properties and content. It skillfully manages permissions and hierarchies within file and folder structures across various data repositories. Through real-time aggregation, normalization, and enrichment of access events, Raptor Eye captures comprehensive insights about user activities and directory services, providing a solid foundation for in-depth security analysis.
Raptor Eye meticulously examines changes in files, pre-assesses the connections between users,
groups, and data, and standardizes these relationships.
It enhances the process by gathering, normalizing,
and augmenting data related to access modifications, configuration changes, and a wide range of system events,
creating a detailed framework of information for security analysis. This process ensures a thorough and meaningful
approach to safeguarding digital environments.
Raptor Eye's SIEM for small businesses is a crucial tool for autonomously identifying potential threats. It eliminates the need for manual oversight and accelerates threat response. By automating and integrating security operations, it streamlines the incident response mechanism. Moreover, it increases operational efficiency and protects against cyber threats with minimal human intervention. This strategic automation and behavioral profiling underscore Raptor Eye's commitment to
delivering advanced cybersecurity for small businesses.