Understanding Zero-Day Attacks: How to Respond
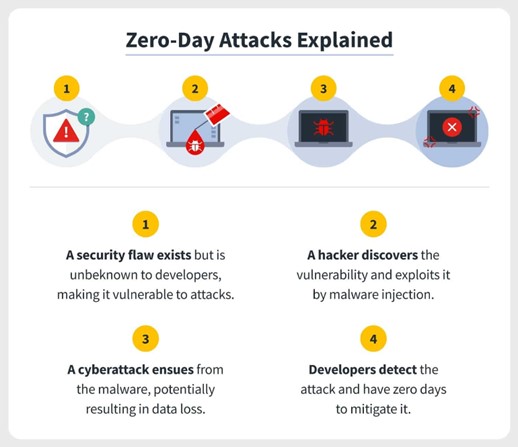
A zero-day attack occurs when cybercriminals exploit an unpatched software vulnerability. Since
the flaw is unknown to the software vendor or security teams, it can be used to deliver malware, steal data, or
compromise systems without immediate detection. These vulnerabilities often remain unnoticed for weeks, months, or
even longer, giving attackers ample opportunity to infiltrate networks. The term “zero-day” refers to the fact
that the developers have zero days to fix the flaw before it's exploited in the wild.
Common Targets of Zero-Day Attacks
- Operating Systems: Windows, Linux, macOS
- Web Browsers: Chrome, Firefox, Internet Explorer
- Plugins and Extensions: Java, Flash, Adobe Acrobat
- Enterprise Software: CRM, ERP, and collaboration platforms
How Zero-Day Attacks Work
- Discovery of Vulnerability: A hacker or researcher uncovers a flaw in a
piece of software or hardware that has yet to be discovered by its developers.
- Exploit Creation: The hacker creates an exploit—a piece of code or a
tool—that leverages the vulnerability.
- Deployment of Attack: The attacker deploys the exploit through various
methods such as phishing emails, malicious websites, or infected downloads.
- Undetected Breach: Since no security patch exists for the
vulnerability, traditional antivirus programs and firewalls may fail to detect the attack, giving attackers
ample time to infiltrate the system.
How to Respond to a Zero-Day Attack
- Implement Intrusion Detection Systems (IDS) and
Intrusion Prevention Systems (IPS): IDS and IPS solutions can help detect suspicious behavior that may
indicate an exploit in action. By analyzing network traffic, these systems can alert your security team to
abnormal patterns that may be linked to zero-day attacks.
- Patch Management: While zero-day attacks
exploit unpatched vulnerabilities, having a robust patch management system in place can reduce your risk. Always
keep your systems, software, and firmware up to date with the latest security patches to minimize exposure to
known vulnerabilities.
- Endpoint Protection and Monitoring:
Endpoint Detection and Response (EDR) solutions provide advanced monitoring of workstations, laptops, and
servers. These tools continuously observe activity on endpoints, enabling the early detection of malicious
behavior that may be related to a zero-day exploit.
- Segmentation and Access Controls: Network
segmentation can limit the spread of a zero-day attack. Implement strict access controls, ensuring that
employees have only the permissions they need to perform their tasks. This will reduce the impact of an exploit
by containing it to smaller segments of your network.
- Incident Response Planning: Prepare for
the possibility of a zero-day attack by creating a comprehensive incident response plan. This plan should
include steps to quickly contain the breach, assess the damage, and notify affected stakeholders. Regularly
simulate attack scenarios to keep your response team ready for real-world situations.
- Zero Trust Architecture: Adopt a
zero-trust approach to security, which assumes that threats may already exist inside your network. This mindset
encourages continuous verification of users and devices before granting access, reducing the chances of an
undetected zero-day exploit.
The Risks and Impact of Zero-Day Attacks
- Data Theft: Sensitive customer information, intellectual property, and
financial data can be stolen, leading to severe reputational and financial damage.
- System Compromise: Attackers can gain control over critical systems,
potentially halting operations or demanding ransom.
- Espionage: Nation-state actors often leverage zero-day attacks for
espionage and surveillance purposes.
Defending Against Zero-Day Attacks
- Regular Software Updates: Keep systems and applications up to date to
minimize the attack surface.
- Behavior-Based Detection: Use advanced threat detection systems that
analyze suspicious behavior, not just known malware signatures.
- Network Segmentation: Isolate critical systems to prevent attackers
from moving laterally within your network.
- Incident Response Plans: Develop a detailed incident response plan to
quickly contain and mitigate the effects of an attack.
- Threat Intelligence Sharing: Join threat intelligence networks to stay
informed about emerging threats.