

In today’s ever-evolving digital landscape, organizations face an increasing number of cyber threats. As businesses rely more on technology, the risk of attacks, such as data breaches, ransomware, and phishing attempts, has grown exponentially. To effectively detect, mitigate, and respond to these threats, many companies are turning to Security Operations Centers (SOC) as a critical part of their cybersecurity strategy.
A Security Operations Center (SOC) is a centralized unit within an organization responsible for continuously monitoring, analyzing, and responding to security incidents. SOCs employ a team of cybersecurity professionals, armed with specialized tools, to detect and neutralize threats in real time.
SOCs work around the clock to ensure that networks, servers, endpoints, databases, and applications are protected from unauthorized access and malicious activity.
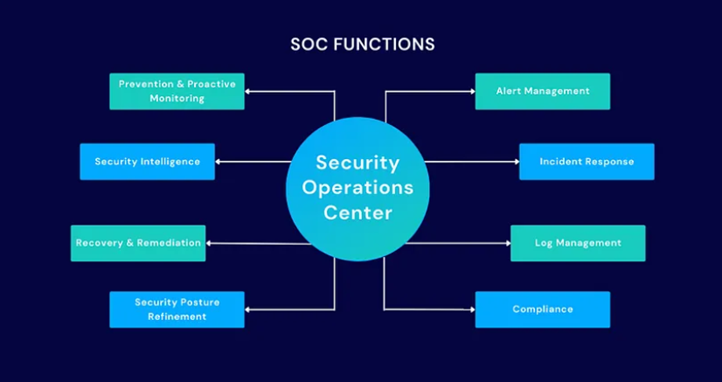
An effective SOC relies on the integration of people, processes, and technology. The key components include:

1. 24/7 Threat Monitoring: Cyberattacks can happen at any time, making it crucial for organizations to have continuous monitoring in place. SOCs operate 24/7 to detect threats in real time, ensuring quick action before an attacker can cause significant damage.
2. Proactive Threat Hunting: A key feature of SOCs is their ability to perform proactive threat hunting. Rather than waiting for security alerts, threat hunters actively search for signs of intrusions or vulnerabilities that have not yet triggered alarms.
3. Incident Response and Mitigation: SOCs handle security incidents by implementing an organized incident response process, including identifying, containing, and mitigating threats while preventing future incidents.
4. Centralized Visibility: SOCs provide a centralized view of all security events across different systems, helping security teams monitor activity from a single location and identify suspicious patterns.
5. Regulatory Compliance: SOCs help businesses achieve and maintain compliance with regulations by ensuring proper security controls are in place and documented.
6. Leveraging Advanced Security Technologies: SOCs use tools such as machine learning, AI, and automated incident response to enhance their detection and response capabilities.
To address these challenges, many organizations use Managed SOC Services or SOC-as-a-Service, outsourcing SOC functions to ensure access to expert personnel and cutting-edge tools.
The Security Operations Center (SOC) is an essential component of modern cyber defense, providing continuous monitoring, proactive threat hunting, and rapid incident response. SOCs enable organizations to identify, mitigate, and recover from cyber threats before they cause significant harm.